Data Security Considerations When Choosing an ERP System for Small Businesses
In today’s digital landscape, data security is critical for small businesses. This article explores essential data security considerations when choosing an ERP system, including encryption, access controls, regular updates, compliance, and vendor reputation. Ensure your business operations remain secure and efficient with the right ERP solution.
Share this Post to earn Money ( Upto ₹100 per 1000 Views )
In today’s rapidly evolving digital landscape, data security has become a critical concern for businesses of all sizes. For small businesses, choosing the right Enterprise Resource Planning (ERP) system is pivotal, as the right choice can streamline operations, improve efficiency, and enhance data security. This post delves into the key data security considerations small businesses must weigh when selecting an ERP system.
Understanding ERP Systems
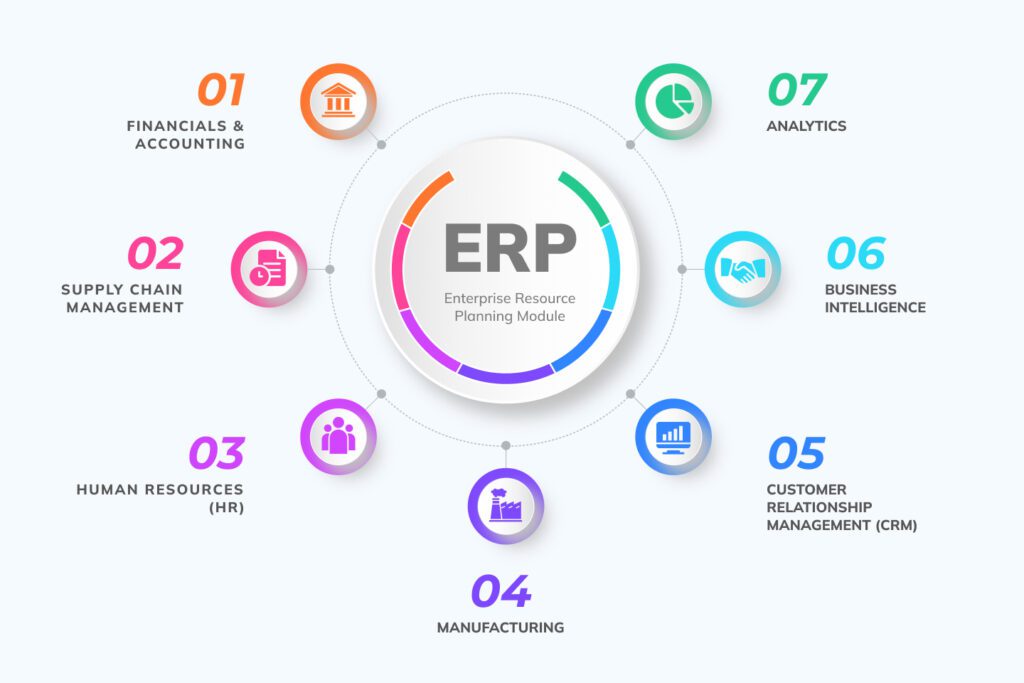
Enterprise Resource Planning (ERP) systems integrate various business processes, enabling seamless data flow across departments. From accounting and human resources to supply chain management and customer relationship management, ERP systems centralize data, enhancing decision-making and operational efficiency. However, this centralization also makes data security paramount.
Key Data Security Considerations

1. Data Encryption
Encryption is a fundamental aspect of data security. It involves converting data into a code to prevent unauthorized access. When choosing an ERP system, ensure it offers robust encryption protocols for data at rest and in transit. This protects sensitive information from being intercepted and deciphered by malicious actors.
2. Access Controls and User Authentication
Access control mechanisms and user authentication are crucial for safeguarding sensitive data. Look for ERP systems that support multi-factor authentication (MFA) and role-based access controls (RBAC). MFA adds an extra layer of security by requiring multiple verification methods. At the same time, RBAC ensures that users can only access data necessary for their roles, minimizing the risk of internal breaches.
3. Regular Security Updates and Patching
Cyber threats are continually evolving, making regular security updates and patching vital. An ERP system provider should have a robust process for deploying updates and patches to address vulnerabilities promptly. Ensure the vendor has a strong track record of maintaining their systems and releasing timely updates.
4. Data Backup and Disaster Recovery
Data loss can be catastrophic for any business. Ensure the ERP system includes comprehensive data backup and disaster recovery plans. Regular backups and a tested recovery plan can mitigate the impact of data breaches, hardware failures, or other disasters, ensuring business continuity.
5. Compliance with Regulations
Different industries have varying regulatory requirements concerning data security and privacy. Ensure that the ERP system complies with relevant regulations such as GDPR, HIPAA, or CCPA. Non-compliance can lead to hefty fines and damage to reputation. The vendor should provide documentation and support to help your business remain compliant.
6. Vendor Reputation and Support
The reputation of the ERP vendor is a critical consideration. Research the vendor’s history, customer reviews, and case studies to gauge their reliability and commitment to data security. Additionally, evaluate the level of support they offer. Responsive and knowledgeable support can be invaluable, especially during security incidents.
7. Customizability and Integration
Every business has unique needs, and the ability to customize and integrate the ERP system with existing applications is essential. However, these customizations and integrations should not compromise data security. Ensure that the ERP system supports secure integration protocols and that any customizations adhere to best security practices.
Implementing Data Security Best Practices
While choosing a secure ERP system is crucial, implementing best practices within your organization is equally important. Here are some steps small businesses can take:
- Employee Training: Educate employees on data security practices, phishing attacks, and the importance of using strong passwords.
- Regular Audits: Conduct regular security audits to identify vulnerabilities and ensure compliance with security policies.
- Incident Response Plan: Develop and test an incident response plan to handle data breaches swiftly and effectively.
Summary
Choosing the right ERP system involves more than just evaluating features and pricing; data security should be at the forefront of your decision-making process. By considering factors such as encryption, access controls, regular updates, compliance, vendor reputation, and support, small businesses can select an ERP system that meets their operational needs and protects their valuable data.
Data security is an ongoing process. Continuously monitor and improve your security measures to stay ahead of emerging threats. With a secure ERP system and robust security practices, small businesses can confidently leverage technology to drive growth and success.








